
Joe Sandbox Cloud

Hypervisor based Inspection on Bare Metal
It is designed to capture a wide range of behavior data including system calls, kernel calls, user mode API calls, access to memory areas and instructions.
Joe Sandbox Hypervisor is implemented as full blown hypervisor without any dependency to open source solutions such as KVM or XEN. Joe Sandbox Hypervisor enables stealth malware analysis on virtual machines as well as on bare metal machines.
Joe Sandbox Hypervisor is a plugin for Joe Sandbox Cloud.

Joe Sandbox Hypervisor Explained
Joe Sandbox Hypervisor is a modular and standalone hypervisor which does not derivate from an existing open source virtualization platform such as KVM and XEN. The hypervisor stealthy captures a wide range of data, including:
- System calls with arguments
- Kernel calls with arguments
- Usermode calls with arguments
- Access to mode memory areas (e.g. PEB)
- Access to performance counters
- Execution of specific instruction (e.g. CPUID) by kernel and user code
Due to its design Joe Sandbox Hypervisor enables analysis of any malware (including kernelmode rootkits) on virtual machines as well as on bare metal machines (real PCs, laptops etc). Malware often evades analysis on virtual machines (not bare metal) by detecting unique virtual machine arifacts. Analysis on bare metal with Joe Sandbox Hypervisor does not have this weakness.
Explore Joe Sandbox Hypervisor
Have a look at the behavior analysis reports generated by Joe Sandbox Hypervisor or contact Joe Security to schedule a technical presentation.
Custom Hypervisor
Joe Sandbox Hypervisor is implemented as a custom hypervisor which does not derivate from virtualization solution such as XEN and KVM. Due to this independence Joe Sandbox Hypervisor can run on any device, including virtual machines as well as bare metal.

Virtual and Physical Analysis Systems
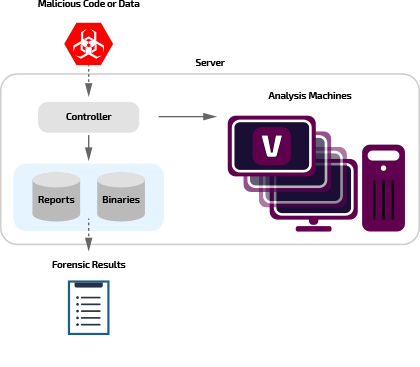
Joe Sandbox Hypervisor enables to use a mix of virtual and physical analysis machines for analysis. Physical machines are very helpful in order to deal with evasive malware which may not run on virtual systems.

Usermode, Kernel and System Call Monitoring
Joe Sandbox Hypervisor captures a wide range of dynamic data: system calls with arguments, kernel calls with arguments, usermode calls with arguments, access to mode memory areas (e.g. PEB), access to performance counters and execution of specific instruction (e.g. CPUID) by kernel and user code. Joe Sandbox's behavior analysis and detection greatly benefits from this extensive data, enabling the deepest analysis possible.

Memory Access Monitoring
Joe Sandbox Hypervisor tracks access to memory areas, such as the Windows process environment block (PEB). Information about read and write greatly increases the chance to better detect and understand malware.

Stealth
Joe Sandbox Hypervisor is running in seperated mode (ring - 1) which is hard for malware to detect. Joe Sandbox Hypervisor enables to run any malware including kernelmode rootkits. Again since Joe Sandbox Hypervisor runs in separate mode it is very difficult to be detected by malware.

Highly Efficient
Joe Sandbox Hypervisor analyzes malware with native speed and does't introduce any latency or delays. Joe Sandbox Hypervisor's code has been optimized to run highly efficient.

Explore Joe Sandbox Hypervisor
Have a look at the behavior analysis reports generated by Joe Sandbox Hypervisor or contact Joe Security to schedule a technical presentation.
