Joe Sandbox v39 Ruby
Joe Security's Blog
Published on: 30.01.2024
Today, we are proud to release Joe Sandbox 39 under the code name Ruby! This release is packed with many new detection signatures and important features to make Joe Sandbox even better.
 |
Our Joe Sandbox Cloud Pro, Basic, and OEM servers have recently been upgraded to Ruby.
In this blog post, we have presented the most important features of Joe Sandbox Ruby, but there are some other interesting features on top:
If you wish to upgrade your on-premise Joe Sandbox installation right away, please read the Update Guide that you received via our e-mailing list. You can also find the Update Guide in our customer portal.
287 new Signatures
Ruby comes with a high number of new Yara and Behavior signatures to detect new malware families like SpectralBlur, PureLand Stealer, KANDYKORN RAT, Hatef Wiper, JaskaGO, Clay Stealer, LambLoad, IronWind, Brook RAT, HazyLoad, PureLog Stealer, LostTrustEncoded, Golden Axe, Tisak and LiveTeam and many more. In addition, we added 5 new Malware Configuration Extractors, e.g. ToxicEye, Neconyd, meduzastealer, poshc2, diceloader to name a few:
Improved OCR Capabilities
For Phishing Joe Sandbox relays on a rich set of different technologies. OCR (Optical Character Recognition) is one of them. In Joe Sandbox 39 we upgraded the engine to have more precise results. The outcome is better phishing detection - especially for initial phishing lures:
Support for Android 13
Joe Sandbox Ruby enables analysts to investigate APKs (Android Application Packages) on latest Android 13:
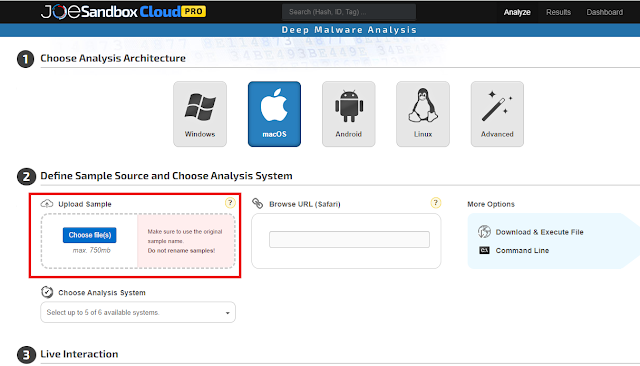
Multi-File Submission for macOS and Linux
We see more and more malware samples which require other files as dependency. If the sample is detonated without the dependencies it won't run and no malicious behavior is analyzed. Joe Sandbox v39 brings now multi-file submission for macOS and Linux. To use multi-file submission simply drag&drop your sample together with the dependencies to the upload mask:
Memory Dumping for Apple Silicon (ARM64)
Joe Sandbox has brought macOS analysis functionality for Apple Silicon in Joe Sandbox v38. With this release Memory Dumping has been added. Memory dumps greatly increases the chance to detect the malware family:
User Menu Redesign
In Ruby we completely redesigned the user menu, making it easier to understand and granting faster access to most important elements of the sandbox:
Final Words
In this blog post, we have presented the most important features of Joe Sandbox Ruby, but there are some other interesting features on top:
- Added powershell upload script
- Added PE file section hash
- Added automated Cloudflare challenges bypass
- Added ETW RPC tracing to improve process trees
- Added LOOKUP events for Apple Silicon (ARM64)
- Added web UI CLI submission support
- Added cookbook command _JBMoveBinLoadingDirectory
- Added support of PROVIDEDBIN placeholder in _JBRunCmd* cookbook commands
- Improved DMG extraction and static analysis
- Improved HTTP session displaying in report HTML
Would you like to try Joe Sandbox? Register for a free account on Joe Sandbox Cloud Basic or contact us for an in-depth technical demo!