Joe Sandbox v33 - White Diamond
Joe Security's Blog
Published on: 29.09.2021
Today we release Joe Sandbox 33 under the code name White Diamond! This release is packed with many new detection signatures and smaller features to make malware detection more precise!
With these brand new behavior, Yara and Behavior signatures, Joe Sandbox is able to precisely detect various new malware families like DBatLoader, ZuRu, Squirrelwaffle, eCh0raix, Kimsuky, REvilLinux, Backstage Stealer, Magniber, BLACKMatter, Lockfile and many more. In addition, we added 13 new malware configuration extractors, e.g. for Revil, Arkei Stealer, Djvu, Cyax Sharp Loader, TelegramRAT, 44CaliberStealer, Tofsee, BitRat, MercurialGrabber, sectopRAT, PhantomMiner, SquirrelWaffle and ApolonSpaceXLoader, just to name a few:
Malware configuration data often includes all C&C as well as other major threat intelligence data (targeted extension for ransomware, ports, login data etc.) making it the malware analyst's gold data.
We also added coverage to detect the latest Microsoft Office CVEs:
The detection signature is fully resistant against obfuscation, which we have seen soon after first exploit attempts:
Finally we have added serval new detection signatures for Android, including: AbereBot, Vultur, Hydra, FlyTrap, S.O.V.A., TEABot and UBEL/Oscrop:
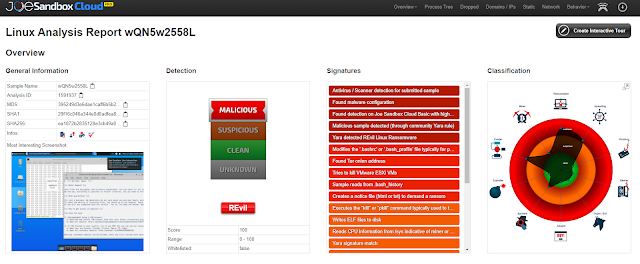
Analysis on Ubuntu 20.04
On top of the existing support for Ubuntu 16.04 and CentOS, White Diamond allows you to analyze Linux based malware on Ubuntu 20.04:
Sigma Extensions
We added support for the pipe_created and module_load Sigma events. As several existing Sigma signatures already use that event, Joe Sandbox benefits from additional detections, e.g. for CobaltStrike:
Atom Bombing / ProGate
Atom Bombing is a relatively new process injection technique. It misuses global atoms to allocate and write memory in remote processes. With White Diamond Joe Sandbox successfully detects this injection technique:
Final Words
In this blog post, we have presented the most important features of Joe Sandbox White Diamond, but there are some other interesting features on top:
- Improved AI Phishing Detection for generic templates
- Improved Yara scanning performance
- Improved Windows Defender shutdown
- Improved Sigma integration
- Improved URL rewriting extraction
- Improved memory dumping
- Improved prevention of RDTSC-based VM detection
Would you like to try Joe Sandbox? Register for a free account on Joe Sandbox Cloud Basic or contact us for an in-depth technical demo!