Joe Sandbox 26.0.0 - Aquamarine is ready!
Joe Security's Blog
Published on: 28.05.2019
We continue our endeavors to make Joe Sandbox the world's best malware analysis system for Windows, macOS, Android, Linux and iOS. Today we release Joe Sandbox 26 under the code name Aquamarine! This release is packed with brand new features and interesting enhancements based on our customers' precious feedback.
Our Joe Sandbox Cloud Pro, Basic and OEM servers have already been upgraded to Aquamarine recently.
If you wish to upgrade your on-premise Joe Sandbox Desktop, Mobile, X, Linux, Complete
or Ultimate installation right away, please run the following command:
Even though we're excited about every aspect of this release, in this blog post we will highlight only a few of our favorite Joe Sandbox Aquamarine features.
If you wish to upgrade your on-premise Joe Sandbox Desktop, Mobile, X, Linux, Complete
or Ultimate installation right away, please run the following command:
mono joeboxserver.exe --updatefast
Even though we're excited about every aspect of this release, in this blog post we will highlight only a few of our favorite Joe Sandbox Aquamarine features.
108 new Behavior Signatures
With 108 new signatures, Joe Sandbox precisely detects the latest threats and evasions! This includes detection of SmokeLoader, xRAT, CobInt, AZORult, LockerGoga, MALXMR, OceanLotus v2, and more:
Report Tour
Sharing is caring! All the Joe Sandbox v26 behavior reports include a new feature which enables every analyst to add comments to the report. This way, you can build a Report Tour which outlines your interpretation of the analysis results. You can then easily share this new custom report with your colleagues and the security community:
Find more information on the Report Tour in one of our recent blog posts.
RDTSC Anti Evasion
RDTSC is a special CPU instruction which queries the Time Stamp Counter (TSC), a 64-bit register present on all x86/64 processors. The time stamp counter allows a very fine grained time measurement. Malware often uses RDTSC to detect virtual machines. For instance, the special CPU instruction CPUID is interrupted by a virtual machine. Due to that, execution takes longer than on real hardware. The difference in execution time is measured with the help of RDTSC:
Joe Sandbox v26 includes a new technology which bypasses virtualization detections that use RDTSC for execution time measurement:
As a result, malware is no longer able to detect virtualization.
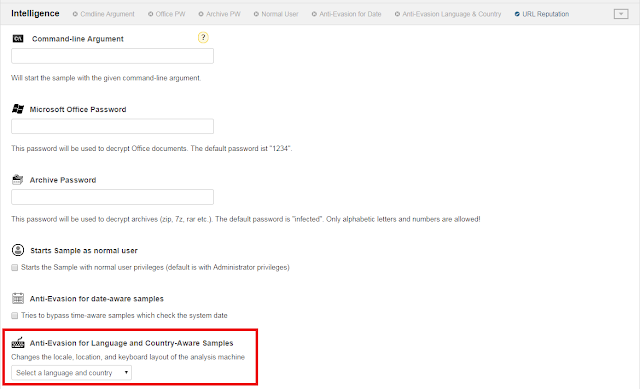
Locale Customization
The number of malware which only executes their payload on specific targets is increasing. In the last months we have seen more and more malware which checks the keyboard language, the locale (a language setting of Windows) as well as the localization setting (e.g. the country):
[Blog] #Malicious #Excel sheets with embedded country-aware #VBA #macros are on the rise! Read our findings we gathered over a period of 4 months:https://t.co/C3yD1znWrQ#malware #dfir pic.twitter.com/lIjWhdjWoZ— Joe Security (@joe4security) March 5, 2019
To make these malware samples execute their payload, we have added new locale submission settings:
Command Line Submission
More and more attacks no longer start with malware, but rather a domain controller is breached and a Powershell command line is launched by the attacker on all end-points. To cover this scenario we added a new Command Line submission option to Joe Sandbox Aquamarine:
Note: Please don't mix this up with the option for command line arguments. That option adds an additional argument to a submitted sample (e.g. sample.exe \install).
The command line submission together with PowerShell Script Block Logging (enabled on all Windows 10 analysis by default) also helps to deobfuscate command lines:
We added a couple of new analysis reports, which are interesting for deep investigation, IOC extraction and hunting:
The Function Logs Reports contains all the low-level system call and Win32 API events in chronological order:
The AMSI Log Report contains raw data extracted via the Microsoft Anti Malware Scan Interface:
The Event Log Report is an XML file containing all Windows Event Logs:
Finally, the PowerShell Event Log is an XML file containing all Events related to PowerShell including Script Block Logging:
We added support for macOS Mojave:
This enables customers to run macOS malware on the latest macOS operating system.
New Reports
The Function Logs Reports contains all the low-level system call and Win32 API events in chronological order:
The AMSI Log Report contains raw data extracted via the Microsoft Anti Malware Scan Interface:
The Event Log Report is an XML file containing all Windows Event Logs:
Finally, the PowerShell Event Log is an XML file containing all Events related to PowerShell including Script Block Logging:
MacOS Mojave Support
This enables customers to run macOS malware on the latest macOS operating system.
Joe Sandbox ML
Dynamic analysis, also known as Sandboxing, is great, but combining dynamic and static analysis is even better. This is why we have added Joe Sandbox ML, which is available as a plugin for Joe Sandbox Aquamarine. Joe Sandbox ML is a static file parser which uses latest AI and machine learning techniques to detect malware:
With Joe Sandbox ML Joe Sandbox detects more malware, especially if the malware does not show any malicious behavior (e.g. because the payload is no longer available on the C&C).
You can find more information on Joe Sandbox ML in one of our recent blog posts.
With Joe Sandbox ML Joe Sandbox detects more malware, especially if the malware does not show any malicious behavior (e.g. because the payload is no longer available on the C&C).
You can find more information on Joe Sandbox ML in one of our recent blog posts.
Final Words
In this blog post, we introduced some of the major features of the Aquamarine release. Furthermore, minor features are:
- Drag & Drop support for Sample Upload
- Opcode based Yara rule downloads in report
- Option to extend analysis time for Remote Assistance
- Improved decoupling of the web application from the back end
- New submission routes in Web API
- SHA-1 and SHA-256 thumbprint for PE Authenticode certificates
- STrace analysis for Android native binaries
- Improved MITRE ATT&CK mapping
What is next? We have an amazing pipeline of new technologies and features - stay tuned!
Want to try Joe Sandbox? Register for Free at Joe Sandbox Cloud Basic or contact us for an in-depth technical demo!