Joe Sandbox v34 Boulder Opal
Joe Security's Blog
Published on: 14.02.2022
Today we release Joe Sandbox 34 under the code name Boulder Opal! This release is packed with many new detection signatures and interesting features to make malware detection more precise!
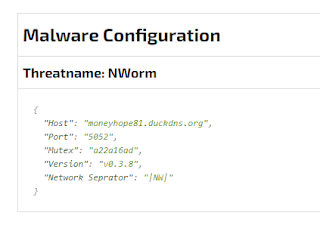
With these brand new Yara and Behavior signatures, Joe Sandbox is able to precisely detect various new malware families like WhisperGate, SilentXMRMiner, UpdateAgent, DeadBolt, onlyLogger, Vulturi Stealer, BotenaGo and many more. In addition, we added 10 new malware configuration extractors, e.g. for Jupyter Backdoor, BlackMatter, VermillionStrike, Stonks Stealer, socelars, DarkStealer, JesterStealer, BlueBot, BluStealer, globeimposter, vulturistealer, Rook Ransomware, NWorm, BlackCat, phoenixkeylogger just to name a few:
Malware configuration data often includes all C&C as well as other major threat intelligence data (targeted extension for ransomware, ports, login data etc.) making it the malware analyst's gold data.
Finally, we have added serval new detection signatures for Android, including L3MON, SharkBot, ERMAC and GriftHors:
Analysis on Windows 10 2004, 20H2 and 21H1
We have extended the support for Windows analyzers to versions 2004, 20H2 and 21H1:
This enables analysts to perform dynamic malware analysis on more recent Windows versions.
Analysis of Hidden Macro 4.0
Boulder Opal brings additional features to extract and deobfuscate Macro 4.0 code from hidden Microsoft Excel sheets:
Full Analysis Report: https://www.joesandbox.com/analysis/566383/0/html#static
This enables to extract more dropper URLs and improve detection.
Sigma Extensions
We have added support for the dns_query Sigma events. As several existing Sigma signatures already use that event, Joe Sandbox benefits from additional detections:
Full Analysis Report: https://www.joesandbox.com/analysis/567681/0/html
In addition Sysmon events are directly parsed from event log sources and matched against Sigma rules.
Unified Report Design
With Boulder Opal analyst benefit from a large restyling and unifying of all Joe Sandbox reports, including full, management and IOC reports:
Analysis on macOS Big Sur
We have extended the support for macOS analyzers to Big Sur:
This enables analysts to perform dynamic malware analysis on this recent macOS version.
ThreatFabric Integration
Due to a new ThreatFabric integration Android analyses benefit from detection enhancements and additional C2:
Full Analysis Report: https://www.joesandbox.com/analysis/565521/0/html
Final Words
In this blog post, we have presented the most important features of Joe Sandbox Boulder Opal, but there are some other interesting features on top:
- Added Security Log for Web App
- Added browsing of QR embedded URLs
- Added time zone information for Analyzer
- Added target ID to process overview
- Added an option to set system wide environment variables (including existing processes)
- Improved and enhanced Memory Dumping on Windows Analyzers
- Improved URL extraction from e-Mails (EML and MSG)
- Improved Sigma bridge
- Improved file dumping
- Upgraded to latest log4j and log4net
Would you like to try Joe Sandbox? Register for a free account on Joe Sandbox Cloud Basic or contact us for an in-depth technical demo!