Joe Sandbox v35 Citrine
Joe Security's Blog
Published on: 05.07.2022
Today we release Joe Sandbox 35 under the code name Citrine! This release is packed with many new detection signatures and interesting features to make malware detection even more precise!
If you wish to upgrade your on-premise Joe Sandbox Desktop, Mobile, X, Linux, Complete
or Ultimate installation right away, please run the following command:
mono joeboxserver.exe --updatefast
215 new Signatures
With these brand new Yara and Behavior signatures, Joe Sandbox is able to precisely detect various new malware families like syslogk, BlackBasta, Record Stealer, Symbiote, SVCReady, PrivateLoader, BPFDoor, BumbleBee and many more. In addition, we added 9 Malware Configuration Extractors, e.g. Allcome Clipbanker, Plead, ColdStealer, Jrat, QVoid Stealer, BlackGuard and Colibri, to just name a few:
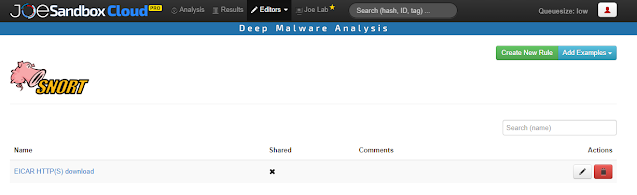
Custom Snort rules
Citrine brings custom Snort rules to Joe Sandbox. Snort rules enable analysts to detect malicious patterns in network traffic. Snort rules can now be added also directly via the web app in the Snort Editor:
Snort rule hits are shown in all analysis reports as well as Live Interaction & Results:
Snort rules are applied to the full network capture but also the decrypted HTTPS traffic! This helps to detect malware even in covert communication.
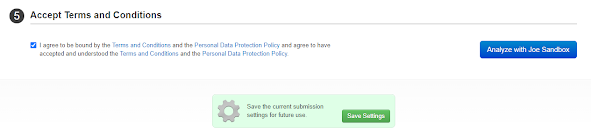
Redesign of Submission Page
We completely redesigned and tidied up the submission page. Important options have been made more prominent, while advanced settings which are not required everyday are initially hidden. This makes it much easier to navigate the page.
Finally you can save your submission settings directly on this page using the green button at the end.
Video Capture
Analysts can now download a video capture of the full analysis. The video gives a more fine grained view compared to the already existing screenshots, enabling the analyst to see more exactly what happens:
LNK File Parser
LNK files are now statically parsed. All information is shown in the "Static File Info" section:
Recent malicious LNK files: https://www.joesandbox.com/search?q=.LNK
Static Extraction of Macro 4.0 code
Citrine includes a static parser to extract Macro 4.0 code. Joe Sandbox already extracts Macro 4.0 code dynamically, however some Excel documents do not start correctly. Thanks to the static parser we still can detect suspicious codes:
Recent malicious Excel files containing Macro 4.0 code: https://www.joesandbox.com/search?q=macro+4.0
Support to launch ISO and IMG Files
We have seen a surge of submissions which come in disk and image format. Joe Sandbox 35 now launches them correctly:
Final Words
In this blog post, we have presented the most important features of Joe Sandbox Citrine, but there are some other interesting features on top:
- Added bypass for new evasion: SMART_GET_VERSION, block network traffic
- Added option to analyze "empty" MSG and EML in Live Interaction mode
- Added PID of loaded sample to Linux and macOS report in runtime messages
- Added new hook function for macOS: SYS_open_dprotected_np
- Improved Web API search
- Improved static analysis of OLE files
- Improved localized Internet anonymization (LIA) iptables management
- Improved macOS kext stability
- Improved macOS PKG unpacking
- Improved SCAE dynamic mappings on Windows
- Improved Windows Crash Dump recovery
- Upgrade to Python3
Would you like to try Joe Sandbox? Register for a free account on Joe Sandbox Cloud Basic or contact us for an in-depth technical demo!