Endpoint Detection¶
Download¶
The most recent version of Joe Sandbox Detect is 5.3.
Select one of the following links to download Joe Sandbox Detect (Click here to see the current version number):
Introduction¶
Joe Security offers a slim Endpoint Client called Joe Sandbox Detect with the following two functionality:
Validation of EDR / XDR alerts: Joe Sandbox Detect automatically analyzes quarantined files of Endpoint Protection and provides deep malware analysis on top of EDR / XDR alerts.
User-spotted Phishing and Malware Reporting: Joe Sandbox Detect enables any user to easily analyze emails with Joe Sandbox and sends a deep malware analysis report to the security team.
Both functionalities can be used in tandem or single.
Endpoint Detection Quarantine Analysis¶
Joe Sandbox automatically monitors your Endpoint Detection quarantine for new files. New files are automatically sent to Joe Sandbox (Cloud or on-premise) and analyzed. On completion the security team is notified who can perform validation.
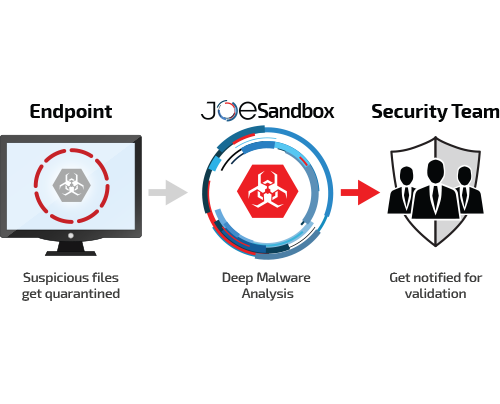
The following Endpoint Detection products are supported:
Avast
AVG
Avira
Crowdstrike
ESET
FortiClient
GData
Kaspersky
MalwareBytes
McAfee
SentinelOne
Sophos
Trendmicro
Windows Defender
Monitoring happens fully automated. No user intervention is required.
Note
Only quarantined files will be submitted for analysis, but not URLs or URL downloads which are blocked by your EDR product.
For Windows Defender please also checkout the Joe Sandbox Microsoft Defender Connector which directly enriches Defender alerts.
Submission of interesting Files¶
Users can easily submit an e-Mail or file for analysis. Simply select the appropriate e-Mail / file and drag it to the analysis area.
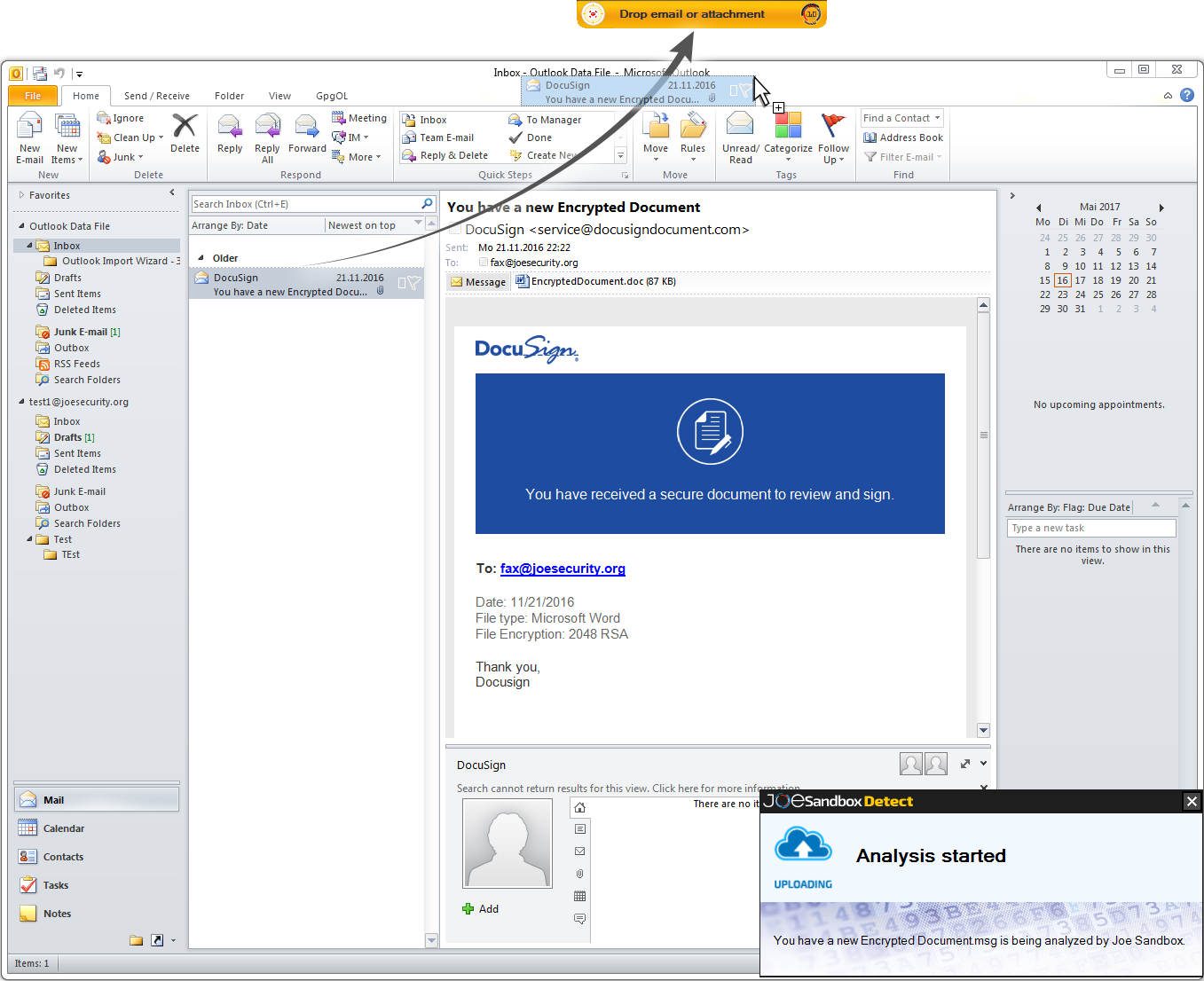
Once the analysis is complete the security team as well as the user are alerted:
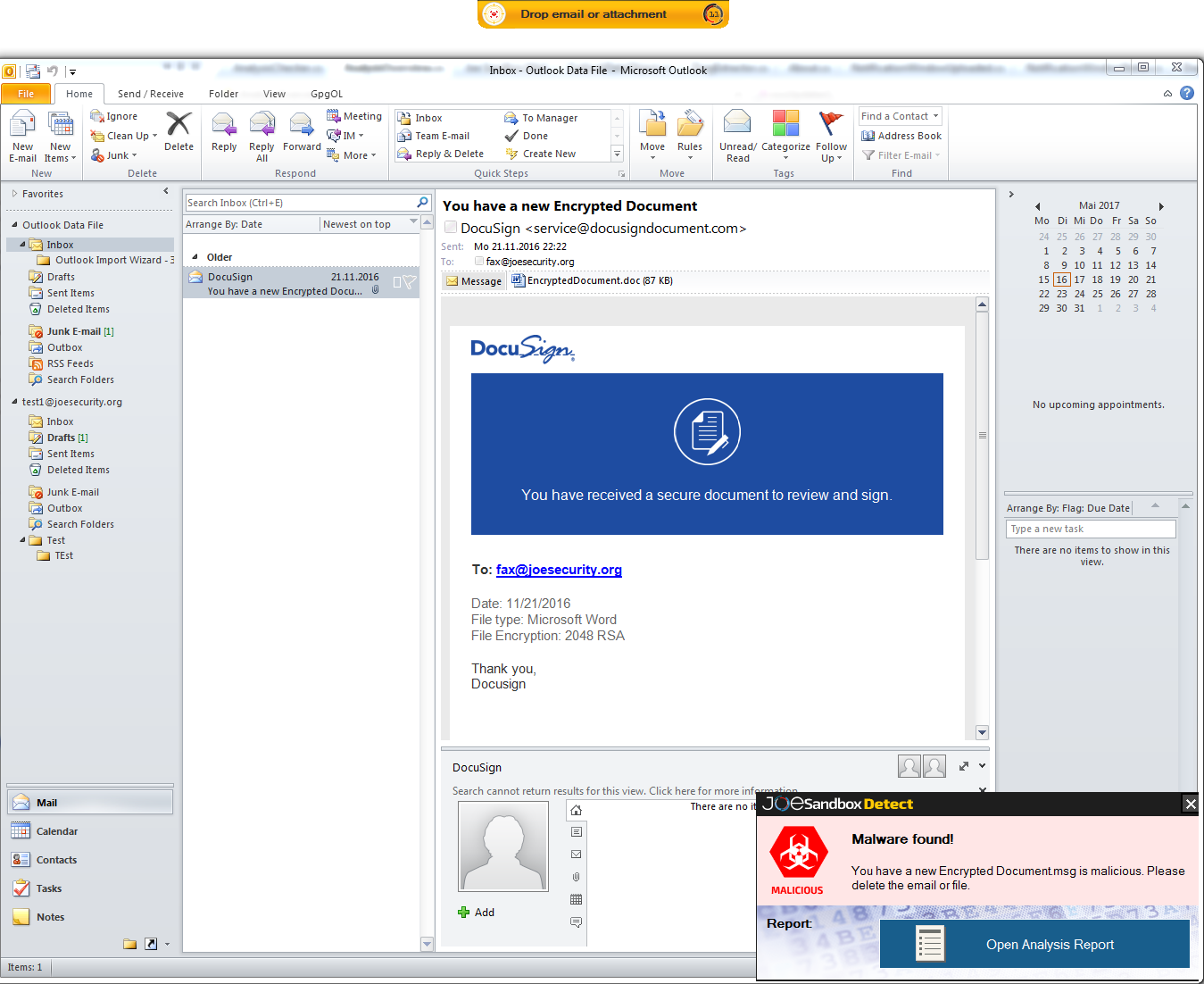
Joe Sandbox Detect classifies the submission into clean, suspicious and malicious:

Note
The suspicious verdict can also have the attribute expert knowledge needed. In that case Joe Sandbox is not sure about the detection. An experienced malware analyst should have a look at the analysis report.
If a user clicks on Open Analysis Report Joe Sandbox Detect will download and show the PDF analysis report.
Note
Joe Sandbox Detect directly connects to your Joe Sandbox (Cloud or on-premise). Hence the security team can access all analysis via the Joe Sandbox web interface. The security team can also download all IOCs, detailed analysis report etc.
Live Interaction¶
If you select the “Live Interaction” option, you will be able interact during the analysis of uploaded files:
Joe Sandbox Detect will automatically open a browser tab as soon as the analysis is ready for Live Interaction.
Create custom Alerts¶
Alerts are e-Mail messages about a malicious or suspicious detection which are sent by Joe Sandbox to the security team. In order to create an alert login into the Joe Sandbox Web interface. Then click on your account and then Filters/Alerts - Alerts. Next click Create New and fill the fields according to the screenshot below:
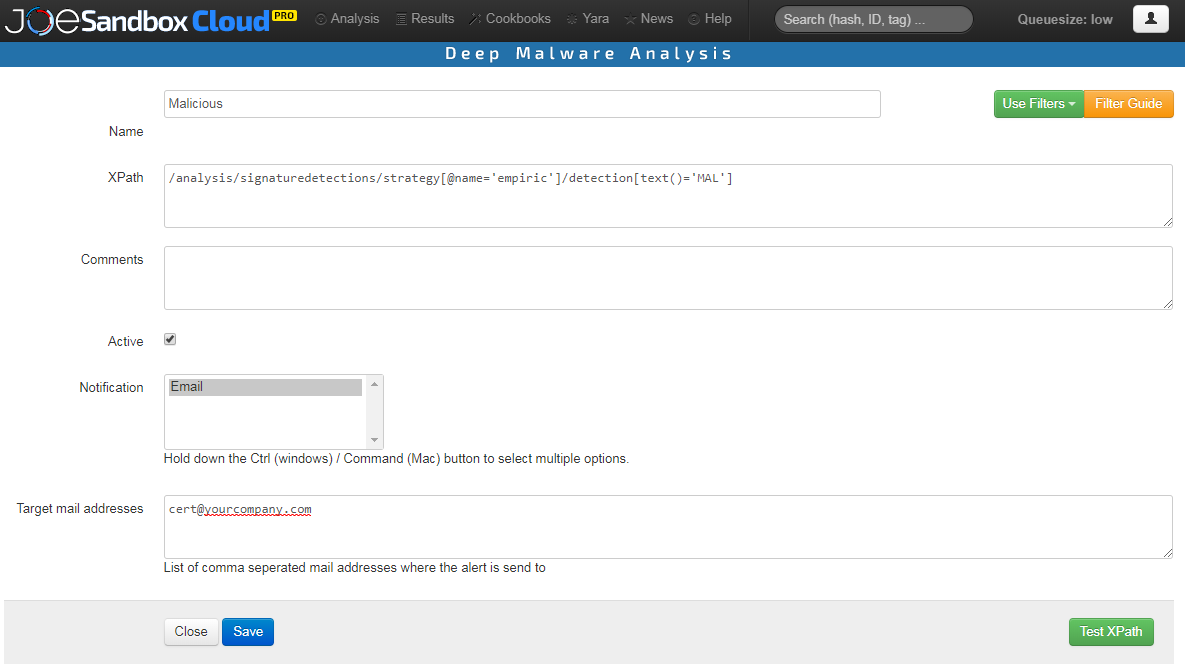
The XPATH filter /analysis/signaturedetections/strategy[@name=’empiric’]/detection[text()=’MAL’] triggers on all malicious detections. /analysis/signaturedetections/strategy[@name=’empiric’]/detection[text()=’SUS’] on all suspicious analyses. You can extend the filter to only trigger on Microsoft Office documents or PDF. To do so please have a look at the Filter Guide which you find on Filters. Once the alert is saved Joe Sandbox will send e-Mail alerts to all e-Mail addresses specified.
Data encryption¶
Joe Sandbox Detect offers the option to encrypt all the analysis data permanently. See the option “ENCRYPTCONFIDENTIALDATA” in the Installation section below.
Data encryption means that:
All the analysis data is encrypted on the server at the end of an analysis.
The encryption key is exclusively stored on the endpoint, i.e. nobody else can decrypt these files except for the user.
If a user downloads a report in Joe Sandbox Detect, the report is decrypted on the fly, so the password does not have to be entered explicitly.
Joe Sandbox use AES-256 encryption with a random 256-bit password for each analysis. There is an option to use pre-define password accross all endpoint.
Please note that meta information (i.e. sample hash, filename, detection status) is not encrypted.
Files from Endpoint Security quarantine are not encrypted.
View Analysis¶
Right click on Joe Sandbox Detect tray icon in your task bar. Then select Show Analysis:
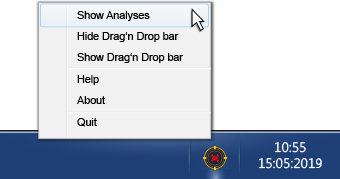
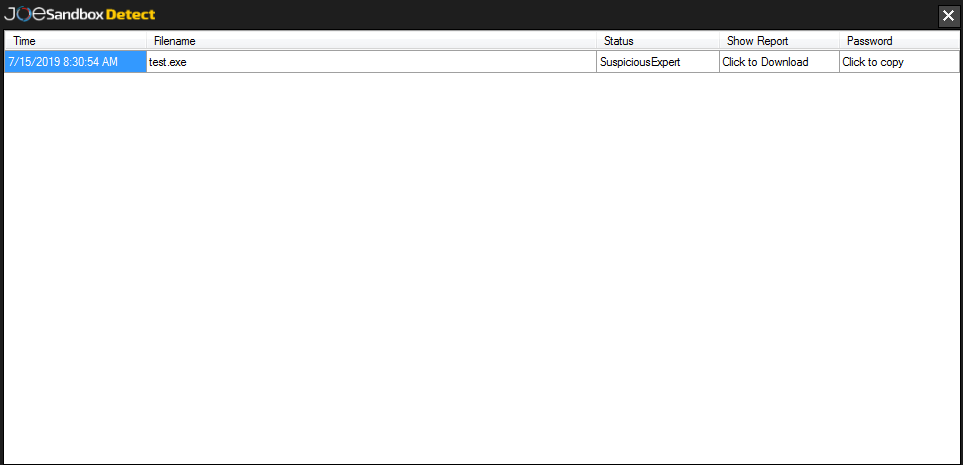
The Analysis Overview will open. You can download the report from there, and also copy the password to the clipboard to be able to decrypt further data (if encryption is used).
Update Joe Sandbox Detect¶
Right click on Joe Sandbox Detect tray icon in your task bar. Then select About:
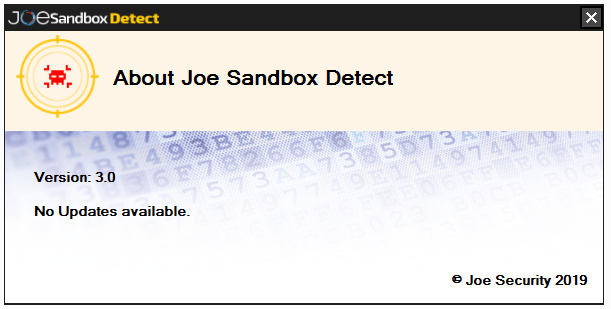
If there is an update available click on the link provided.
Security disclaimer¶
Warning
Joe Sandbox Detect detects malicious e-mails, attachments and files, however does not delete or remove them. You are responsible for deleting and removing malicious files and e-mails. Also be aware that Joe Sandbox is not perfect. An e-mail, attachment or file detected as clean does not warrant that there is no maliciousness!
Installation¶
Download and install the Joe Sandbox Detect installer provided by Joe Security. During installation the installer will ask you for the API key. You find the API key in Web App - User Settings:
Parameter |
Format |
Mandatory |
Default |
Description |
|---|---|---|---|---|
/q |
no |
Enable silent install, without any GUI. |
||
API_KEY |
string |
yes |
API key generated via Web App - User Settings. |
|
ACCEPT_EULA |
integer, yes=1 |
yes |
0 |
EULA available in the Web App - Analyze. |
JBX_SYSTEM |
string |
no |
W10x64_office |
Default analysis system, list of systems can be found in Web App - Analyze - Analysis System. |
JBX_URL |
string |
no |
Joe Sandbox Cloud |
URL to Joe Sandbox web interface, default set to Joe Sandbox Cloud. |
ENCRYPTCONFIDENTIALDATA |
boolean |
no |
false |
All analysis data is encrypted immediately after an analysis. Meta information is kept. Quarantine uploads are not encrypted. |
DEFAULTENCRYPTIONKEY |
string |
no |
If ENCRYPTCONFIDENTIALDATA is true, this key encrypts all analyses; if not set, a new random password is generated for each submission. |
|
NOTIFICATIONWINDOWREPORTDOWNLOAD |
string, “html”, “lighthtml” or “executive” |
no |
executive |
The report type which user can download in the notification window. |
ANALYSISOVERVIEWREPORTDOWNLOAD |
string, “html”, “lighthtml” or “executive” |
no |
executive |
The report type which user can download in the analysis overview. |
ENABLEQUARANTINEUPLOADS |
boolean |
no |
true |
Enables quarantine upload. |
DISABLEMANUALUPLOAD |
boolean |
no |
false |
Disables manual upload. |
REBOOT |
string “Force” |
no |
If set, the computer is rebooted immediately after installation to launch the app as the local user. |
Example:
msiexec /q /i "Joe Sandbox Detect Installer.msi" API_KEY=12a4... ACCEPT_EULA=1 JBX_SYSTEM=w7x64 REBOOT=Force
Error Analysis¶
Joe Sandbox Detect creates log files in C:\ProgramData\Joe Sandbox Detect. In case of an error or application crash please send all logs from C:\ProgramData\Joe Sandbox Detect to Joe Security.
